TightGate protection concept
Protection against attacks from the Internet
Protection against data theft and industrial espionage!
Despite many defence measures, there is hardly any protection against attacks from the Internet that penetrate a network via e-mail attachments or surfing the Internet. Above all, security holes in the internet browser are a central point of attack.
If malicious code enters the internal network through a security hole in the web browser, attackers gain far-reaching access to sensitive data and applications. There is a threat of system failure, manipulation, sabotage and industrial espionage.
Where classic security fails
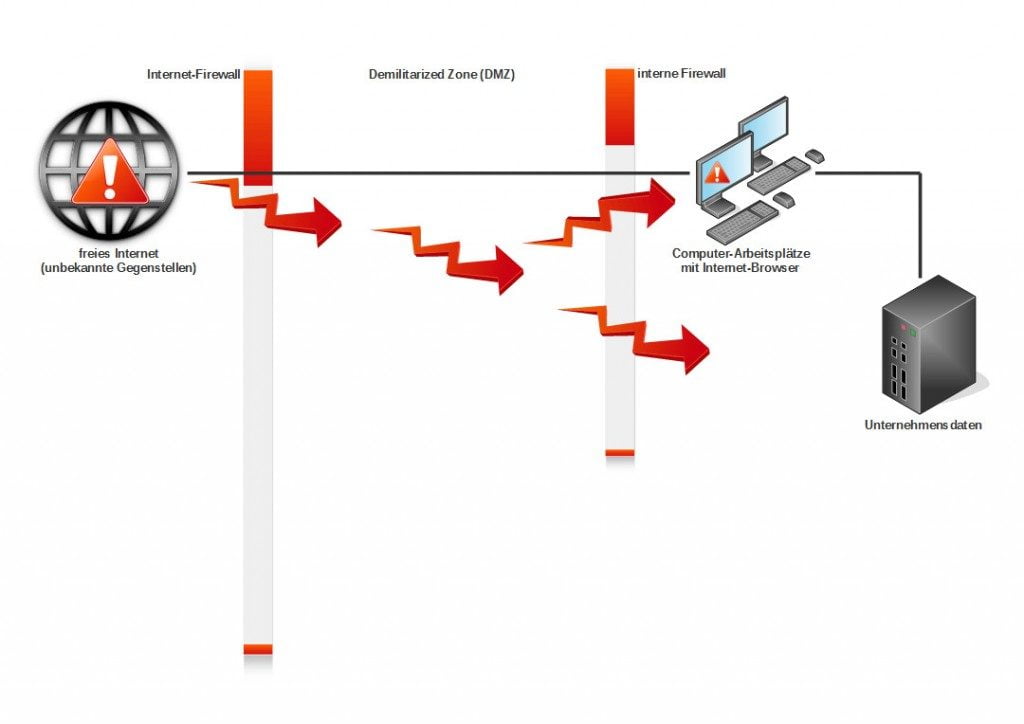
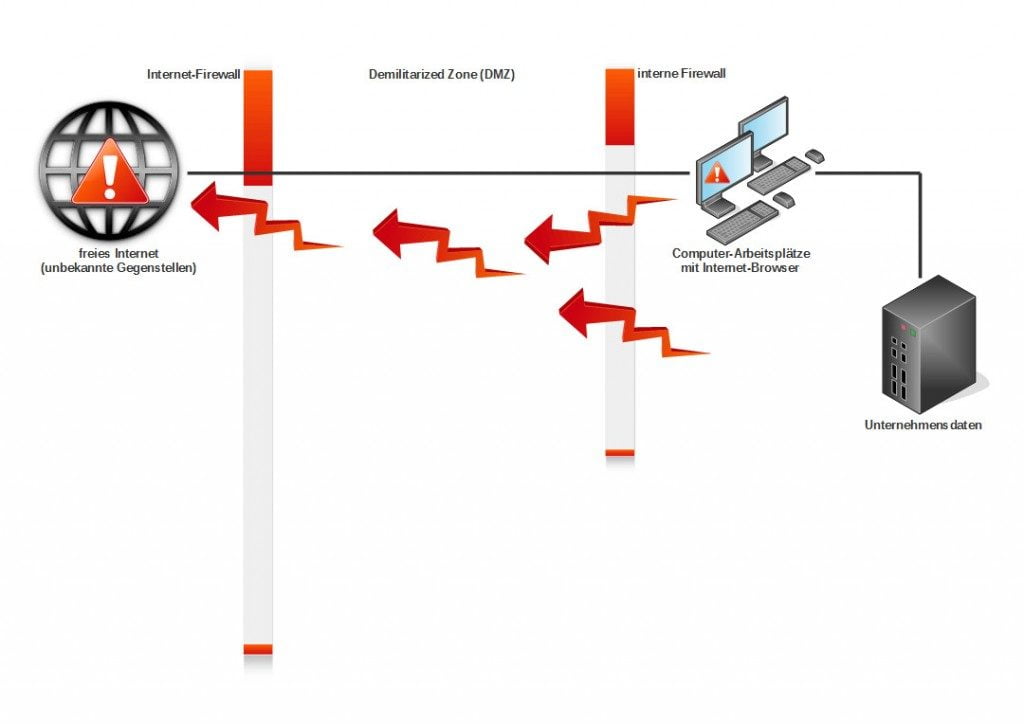
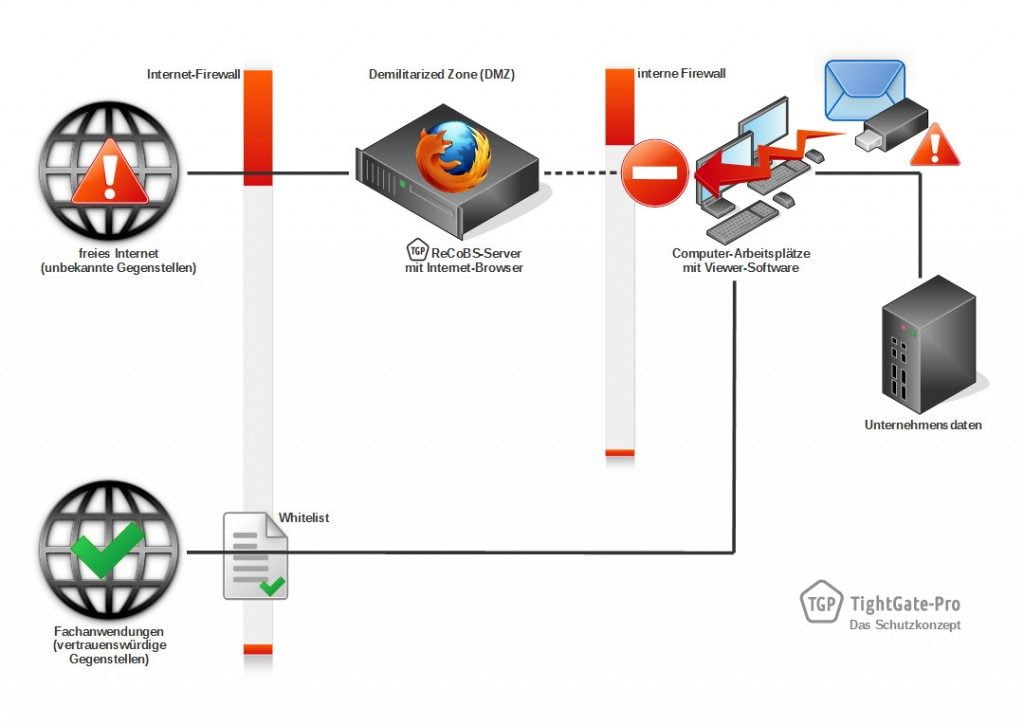
In classic networks, the browser is run on the internal network at the workplace . This means that potentially malicious web content from the internet is interpreted there, where it can cause a wide range of damage (see Figure 1). It does not matter whether the browser is executed on PCs, in VDI environments or locally virtualised. In all cases, the separation from the internal IT environment is weak. As a result, there is a risk of data theft, blackmail and sabotage. For example, malicious code that has entered the internal corporate network can leak corporate data via the browser (see Figure 2).
The technically feasible, complete separation of internal networks from the internet (double network) is hardly an option for operational reasons. After all, Internet searches are part of everyday business life and are indispensable for central processes of production, administration and communication. Internet offers and multimedia applications must therefore remain available and functional at all times!
Conventional measures such as filtering URL addresses or blocking certain content, onthe other hand, offer no security. They do not increase security and also entail high administrative costs. Above all, they work purely statically and do not combat the cause of the problem. This is because even serious websites often fall victim to compromise without the knowledge of the operators and turn into veritable “malware slingshots”.
Defence measures such as intrusion detection systems (IDS) or virus scanners also only provide limited protection, as they only specialise in known attack patterns. However, new malicious codes and attack strategies enter circulation worldwide every day: an ultimately futile cat-and-mouse game for the reactive protection systems.
Security vulnerabilities in internet-linked applications in 2021!
The solution
The ideal web browser has Internet access, but should not jeopardise internal data and resources. Consequently, it must not be executed in the internal network, but at the same time it must be usable from the workplace. These requirements, which at first sight seem incompatible, are implemented with the TightGate-Pro Remote Controlled Browser System (ReCoBS) in a way that is both flawless in terms of security and very convenient.
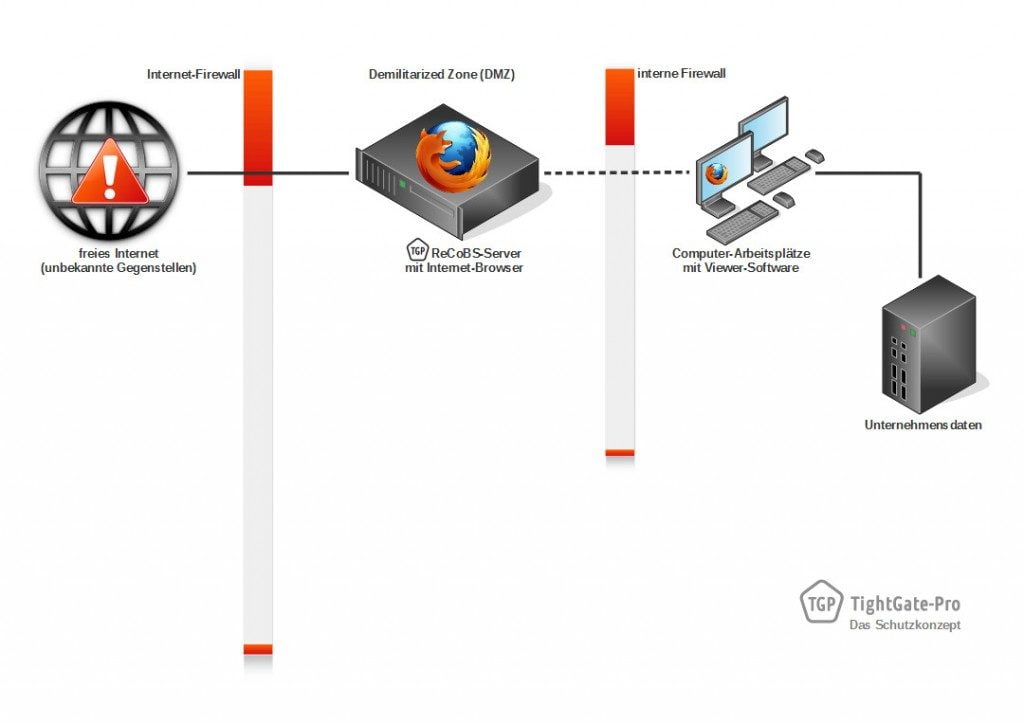
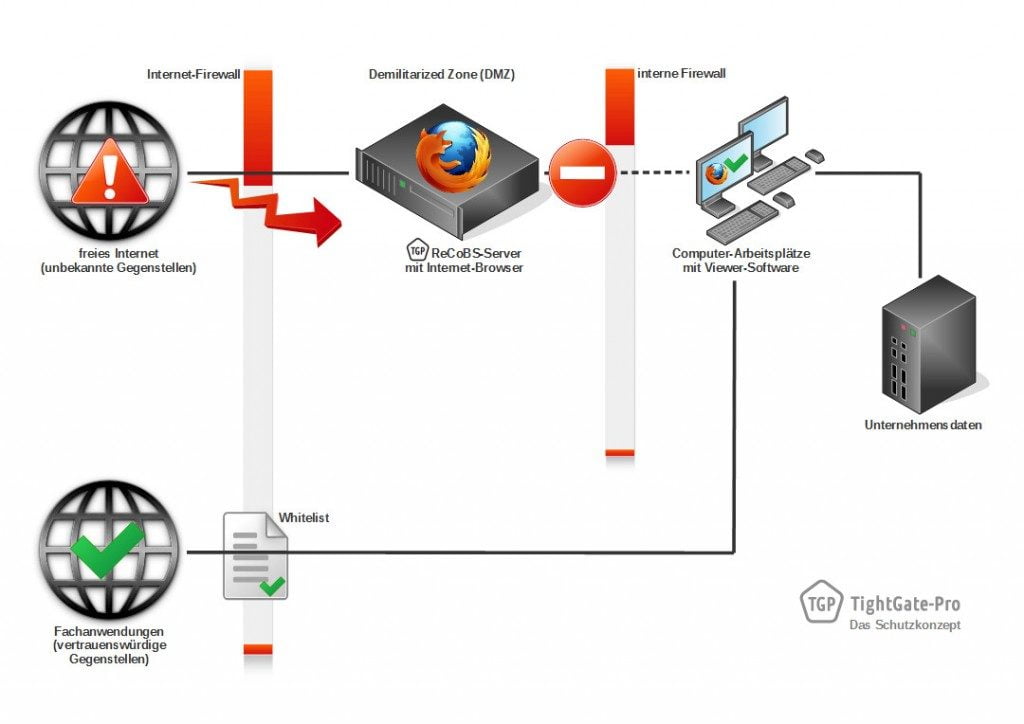
With TightGate-Pro, the browser is not executed in the internal network, but within the DMZ on the dedicated ReCoBS server (see diagram 3). The screen content relevant to the user is transmitted to the workstations in encrypted form in the form of image and sound data streams. Conversely, remote control of the browser is possible from the workstation. The internet can be used in a fully functional way.
The decisive security plus: now the internal network can be completely sealed off from the open Internet via suitable firewall rules. It is therefore in principle inaccessible to attackers from the Internet. In the opposite direction, unwanted data outflow is reliably prevented. This is how you achieve effective protection against attacks from the Internet.
TightGate-Pro implements a user-friendly two-browser solution:
- The open Internet is available risk-free via TightGate-Pro.
- An intranet is accessible via a locally installed browser.
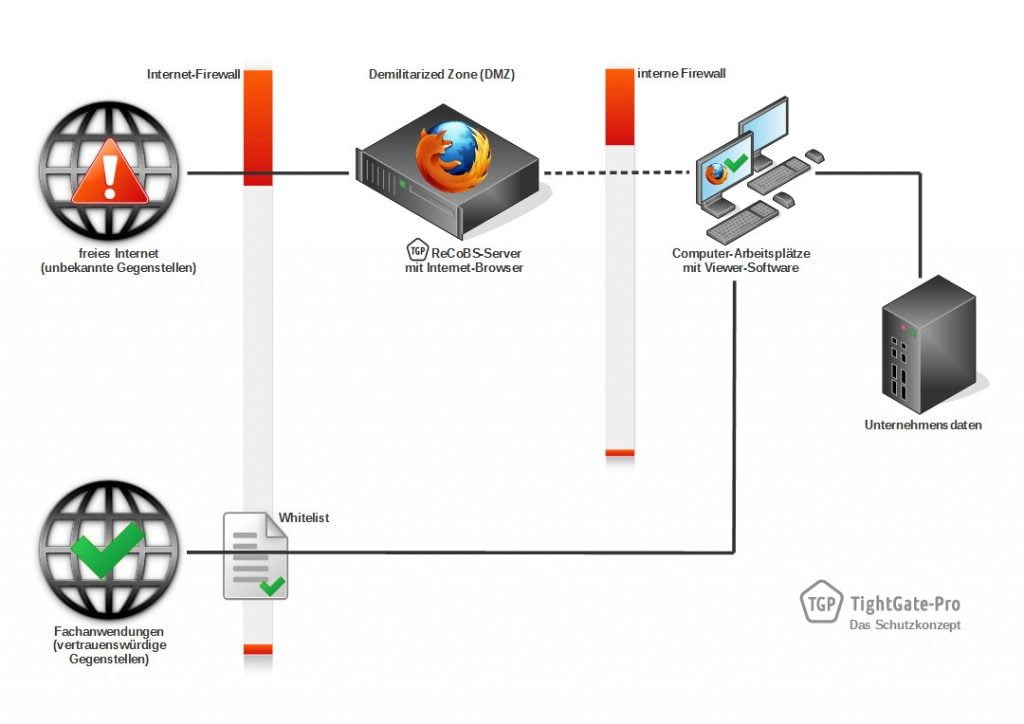
The local browser, which is for internal use only, can be selected as desired. Since it does not have Internet access, the internal network is not endangered. All specialised applications via trusted peers can be enabled using a whitelist in the Internet firewall (see Chart 4).
One more thing… Mobile computers or workstations in the home office are no less in need of protection than stationary workstation computers. However, their network connection via WLAN or LTE has latencies or lower data throughput. This makes it difficult to use the Internet via TightGate-Pro.
With TightGate-Mobile, m-privacy GmbH provides a virtual environment that isolates the vulnerable internet browser on mobile computers. This means that secure Internet use while travelling, with business partners or in the home office is no longer a problem.
TightGate-Pro as a central security module
With TightGate-Pro, the Internet browser is executed on the ReCoBS server, and the screen output is displayed on the monitor of the workstation computer.
Due to this physical separation, even calling up a compromised Internet page has no consequences for the internal network. No damage can be caused by drive-by downloads or links from phishing e-mails (link spoofing). Internal company data always remains protected from attacks from the Internet (see Figure 5).
Even the accidental opening of attachments, calling up dangerous websites or following questionable links does not give an attacker from the Internet access to internal data.
With TightGate-Pro, Internet use is comfortable and attacks from the Internet, spying and industrial espionage are effectively prevented.
Security and Availability
TightGate-Pro makes Internet use secure and at the same time protects against unintentional data leakage – even if malicious code should enter the internal network via other paths. This is because USB sticks or e-mail attachments can also contain malicious code. If this malware tries to download further code from the Internet or send internal data, it will fail. The TightGate protection concept with TightGate-Pro blocks the way. (see diagram 6).
The extensive hardening of the ReCoBS server TightGate-Pro makes it a two-tier protection system. The first level of extensive operating system hardening measures prevents the ReCoBS server from being compromised by attacks via the internet browser. The second level of protection is the physical separation of the internal network from the internet via the function-specific protocol, which is almost insurmountable for attackers.
With the TightGate protection concept and the TightGate-Pro security module, the safe and comfortable use of the Internet becomes a reality – with a high level of protection and permanent availability at the same time.