TightGate-Schutzkonzept
Schutz vor Angriffen aus dem Internet
Schutz vor Datendiebstahl und Wirtschaftsspionage!
Trotz vieler Konzepte zum sicheren Surfen gibt es kaum Schutz vor Angriffen aus dem Internet, die über E-Mail-Anhänge oder das Surfen im Internet in ein Netzwerk eindringen. Vor allem Sicherheitslücken im Internetbrowser sind ein zentraler Angriffspunkt.
Gelangt Schadcode durch eine Sicherheitslücke im Webbrowser in das interne Netzwerk, erhalten Angreifer weitreichenden Zugriff auf sensible Daten und Anwendungen. Es drohen Systemausfall, Manipulation, Sabotage und Wirtschaftsspionage.
Wo klassische Sicherheit versagt hilft eine Zwei-Browser-Strategie
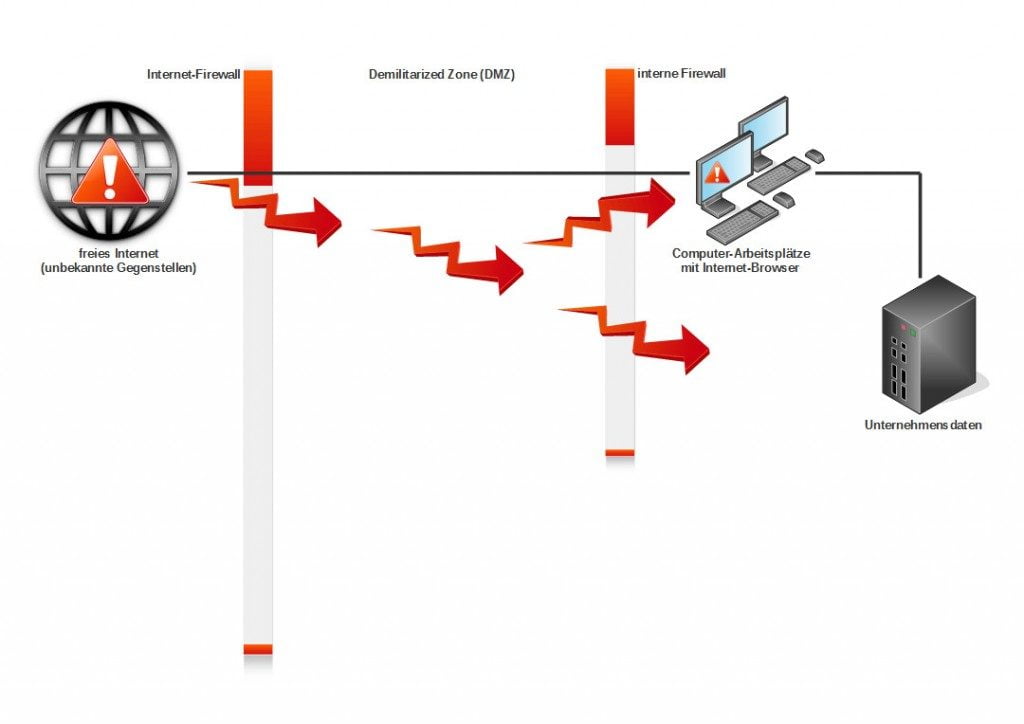
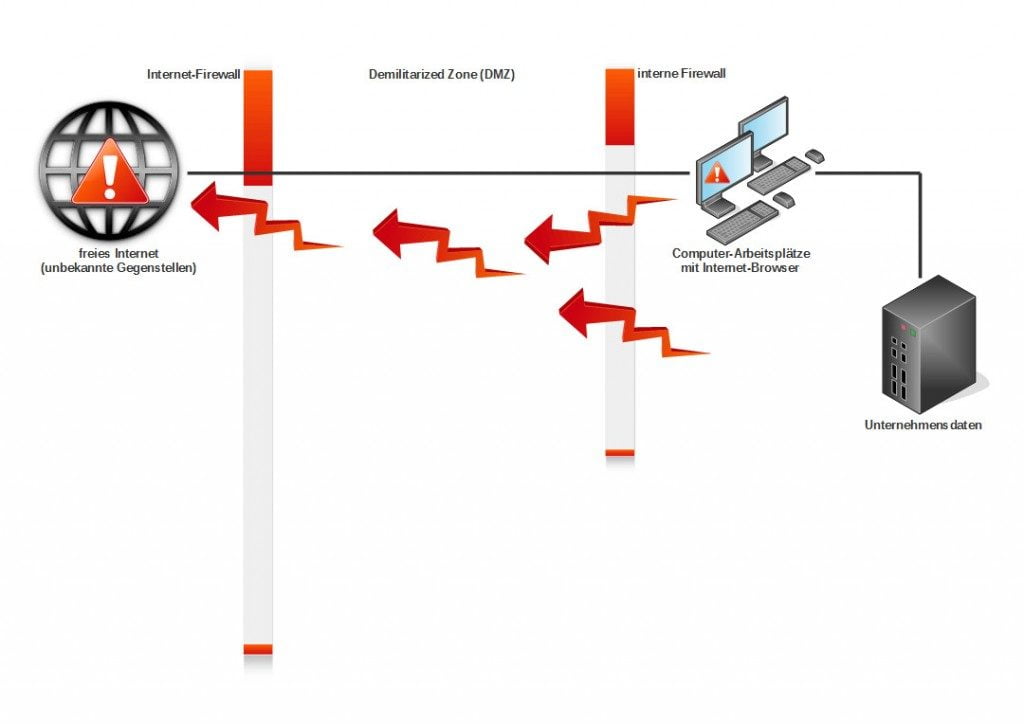
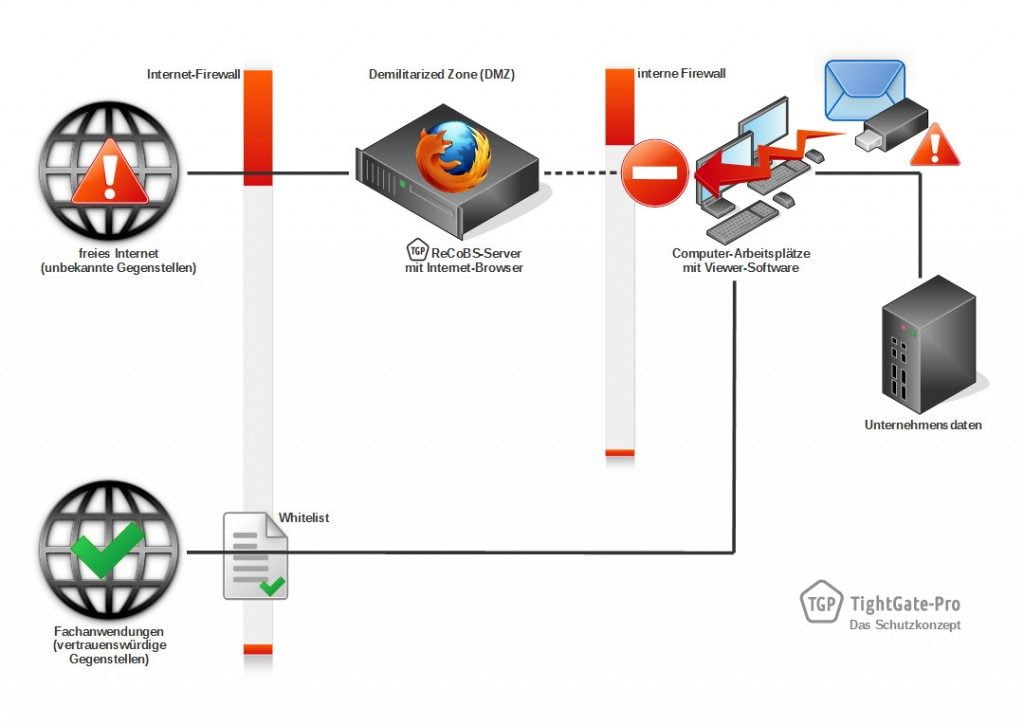
In klassischen Netzwerken wird der Browser im internen Netzwerk am Arbeitsplatz ausgeführt. So werden potenziell bösartige Webinhalte aus dem Internet dort interpretiert wobei sie vielfältigen Schaden anrichten können (siehe Schaubild 1). Dabei spielt es keine Rolle, ob der Browser direkt einem PCs läuft, in Terminal-Server-Umgebungen betrieben oder lokal virtualisiert ausgeführt wird. Denn in allen Fällen ist die Trennung von der internen IT-Umgebung nur schwach. In der Folge drohen Datendiebstahl, Erpressung und Sabotage. So kann Schadcode, der in das interne Unternehmensnetz gelangt ist Unternehmensdaten über den Browsers abfließen lassen (Siehe Schaubild 2).
Die technisch machbare, vollständige Trennung interner Netzwerke vom Internet (Doppeltes Netzwerk) kommt aus betrieblichen Gründen kaum noch infrage. Denn Internetrecherchen gehören zum Unternehmensalltag und sind unerlässlich für zentrale Prozesse der Produktion, Verwaltung und Kommunikation. Internetangebote und Multimedia-Anwendungen müssen daher jederzeit verfügbar und Funktional bleiben!
Keine Sicherheit hingegen bieten konventionelle Maßnahmen wie das Filtern von URL-Adressen oder das Blocken bestimmter Inhalte. Sie erhöhen die Sicherheit nicht und bringen zusätzlich hohen Administrationsaufwand mit sich. Vor allem arbeiten sie rein statisch und bekämpfen nicht die Ursache des Problems. Denn oft werden auch seriöse Websites ohne Wissen der Betreiber Opfer von Kompromittierung und wandeln sich zu regelrechten „Malware-Schleudern“.
Abwehrmaßnahmen wie Intrusion Detection Systeme (IDS) oder Virenscanner schützen ebenfalls nur begrenzt, da sie nur auf bekannte Angriffsmuster spezialisiert sind. Weltweit gelangen jedoch täglich neue Schadcodes und Angriffsstrategien in den Umlauf: ein letztlich aussichtsloses Katz-und-Maus-Spiel für die reaktiven Schutzsysteme.
Sicherheitslücken in Webbrowsern 2022
Der Lösungsansatz - Die Zwei-Browser-Strategie
Der ideale Webbrowser hat zwar Internetzugang, soll aber interne Daten und Ressourcen nicht gefährden. Er darf folglich nicht im internen Netz ausgeführt werden, muss jedoch zugleich vom Arbeitsplatz aus nutzbar sein. Diese auf den ersten Blick unvereinbaren Anforderungen werden mit dem Remote-Controlled Browser-System (ReCoBS) TightGate-Pro im Rahmen einer Zwei-Browser-Strategie sicherheitstechnisch einwandfrei und sehr komfortabel umgesetzt.
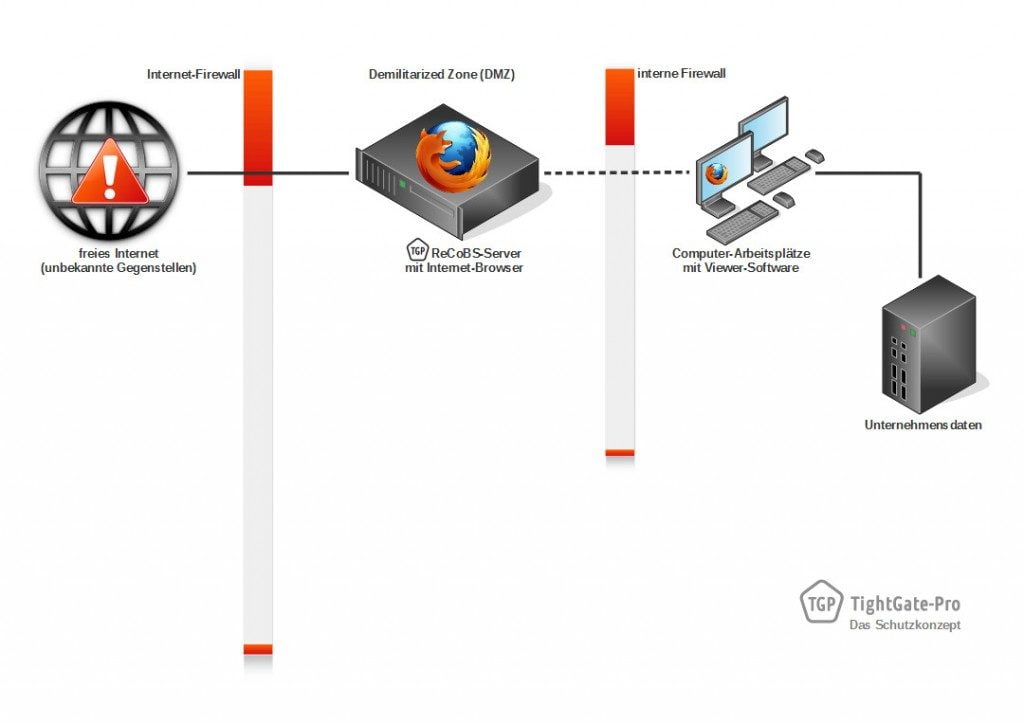
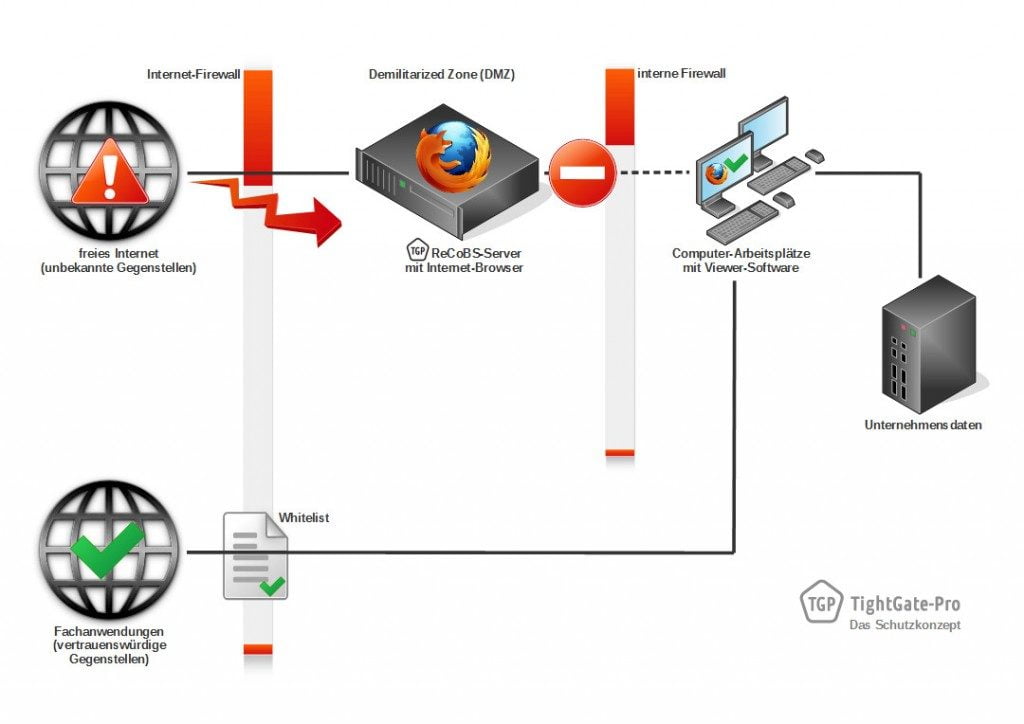
Bei TightGate-Pro wird der Browser nicht im internen Netzwerk, sondern innerhalb der DMZ auf dem dedizierten ReCoBS-Server ausgeführt (siehe Schaubild 3). Der für den Anwender relevante Bildschirminhalt wird in Form von Bild- und Tondatenströmen verschlüsselt an die Arbeitsplatzrechner übertragen. Umgekehrt ist eine Fernsteuerung des Browsers vom Arbeitsplatz aus möglich. Das Internet kann voll funktional genutzt werden.
Das entscheidende Sicherheitsplus: Jetzt kann das interne Netzwerk über geeignete Firewall-Regeln vollständig gegenüber dem offenen Internet abgeschottet werden. Es ist damit für Angreifer aus dem Internet prinzipiell unerreichbar. In der Gegenrichtung wird ungewollter Datenabfluss zuverlässig unterbunden. So erreichen Sie einen effektiven Schutz vor Angriffen aus dem Internet.
TightGate-Pro implementiert eine benutzerfreundliche Zwei-Browser-Lösung:
- Das offene Internet steht über TightGate-Pro risikofrei zur Verfügung.
- Ein Intranet ist über einen lokal installierten Browser zugänglich.
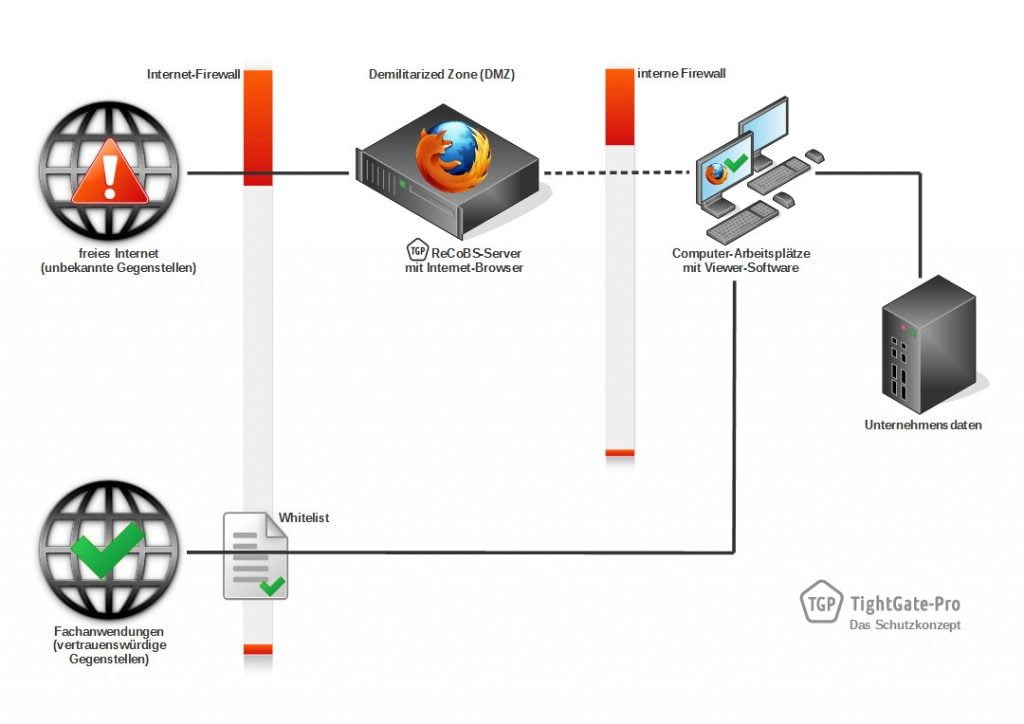
Der nur zum internen Gebrauch vorgesehene, lokale Browser kann beliebig ausgewählt werden. Da er über keinen Internetzugang verfügt, wird die Gefährdung des internen Netzwerks ausgeschlossen. Alle Fachanwendungen über vertrauenswürdige Gegenstellen können anhand einer Whitelist in der Internet-Firewall freigeschaltet werden (siehe Schaubild 4).
Mit TightGate-Mobile stellt die m-privacy GmbH eine virtuelle Umgebung bereit, die den gefährdeten Internetbrowser auf Mobilrechnern isoliert. So ist die sichere Internetnutzung auf Reisen, bei Geschäftspartnern oder im Homeoffice kein Problem mehr.
TightGate-Pro als zentraler Sicherheitsbaustein
Der Internetbrowser wird bei TightGate-Pro auf dem ReCoBS-Server ausgeführt, die Anzeige der Bildschirmausgabe erfolgt auf dem Monitor des Arbeitsplatzcomputers.
Aufgrund dieser physischen Trennung bleibt selbst der Aufruf einer kompromittierten Internetseite für das interne Netzwerk folgenlos. Durch Drive-by-Downloads oder Links von Phishing-E-Mails (Link-Spoofing) kann kein Schaden entstehen. Interne Unternehmensdaten bleiben vor Angriffen aus dem Internet immer geschützt (siehe Schaubild 5).
Auch das versehentliche Öffnen von Anhängen, das Aufrufen von gefahrenträchtige Webseiten oder das Folgen fragwürdigen Links verschafft einem Angreifer aus dem Internet keinen Zugang zu internen Daten.
Mit TightGate-Pro ist die Internetnutzung komfortabel möglich und Angriffe aus dem Internet, Ausspähung und Wirtschaftsspionage werden effektiv verhindert.
Sicherheit und Verfügbarkeit
TightGate-Pro macht die Internetnutzung sicher und schützt zugleich vor unbeabsichtigtem Datenabfluss – selbst wenn über andere Wege Schadcode ins interne Netzwerk gelangen sollte. Denn auch USB-Sticks oder E-Mail-Anhänge können bösartigen Code enthalten. Sollte diese Schadsoftware versuchen weiteren Code aus dem Internet nachladen oder interne Daten versenden, scheitert Sie. Denn das TightGate Schutzkonzept mit TightGate-Pro versperrt den Weg. (siehe Schaubild 6).
Die umfangreiche Härtung des ReCoBS-Servers TightGate-Pro macht diesen zu einem zweistufigen Schutzsystem. Die erste Stufe von weitreichenden Maßnahmen zur Härtung des Betriebssystems verhindert eine Kompromittierung des ReCoBS-Servers durch Angriffe über den Internetbrowser. Die zweite Schutzstufe ist die physische Trennung des internen Netzwerks vom Internet über das funktionsspezifischen Protokolls, welches für Angreifer nahezu unüberwindbar ist.
Mit dem TightGate Schutzkonzept und dem Sicherheitsbaustein TightGate-Pro wird die gefahrlose und komfortable Nutzung des Internets Realität – bei zugleich hohem Schutz und dauerhafter Verfügbarkeit.
Ihr Ansprechpartner

Lars Lehmann
Leiter Vertrieb
Telefon: +49 30 243423-35
E-Mail: l.lehmann@m-privacy.de